Avoiding Phishing and Social Engineering Attacks
What should you do if you’re involved in a phishing attack?
Don’t click! If you feel like something isn’t right, you shouldn’t click on a link or attachment or give out sensitive information.
Never Reuse Passwords
Whether you are working from home or in the office you must make sure the passwords you use are unique to you and not easy to guess.
Reusing passwords increases the potential damage that a data breach could cause. If an attacker manages to gain unauthorized access to your password on one account, they will then have access to all of your accounts that use the same credentials.
Create Strong Passwords
The passwords you use should be unique for each account and difficult for a potential attacker to guess. You should never share your passwords with anyone.
- Use Passphrases. A strong password doesn’t have to be hard for you to remember. Simply memorize a series of unrelated words and combine them together into a passphrase.
- Easy to remember, hard to guess. If you have an easy to remember password you will not have to write it down, reducing the opportunity that someone will find your written password. Ideally the password you make should not contain any personal details about you such as birthdays or the names of children/pets.
Beware of Eavesdropping and Shoulder Surfing
Working remotely comes with its fair share of freedoms. The ability to work from anywhere is a great perk but it’s also a significant security risk. If you decide to leave home to work in a public space, you should be mindful of who has a line-of-sight towards your laptop. You should also refrain from openly discussing sensitive company topics when working in public.
Beware of Public Wi-Fi
- Attackers could make a “honeypot” where they spoof an existing hotspot. Once you connect to their hotspot they can perform a man-in-the-middle (MITM) attack to intercept your connection with a fake domain that looks like the one you were trying to visit. Once you login to the fake domain they now have your login credentials.
- Traffic Sniffing. Other users of the hotspot could potentially see your traffic on unencrypted websites if the provider of the public Wi-Fi does not have adequate security controls in place.
Hacking, phishing, and malware incidents are becoming the number one cause of security breaches today. But, what’s more troubling, these hacking attempts are the result of human errors in some way. Education and awareness are critically important in the fight against cybercriminal activity and preventing security breaches.
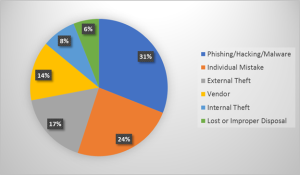
By following these best practices, end users can contribute to a more secure computing environment.

